Todd’s Interview: “Questions Raised about Police Response in Capitol Shooting”
27 Sunday Oct 2013
Posted in EMERGENCY MANAGEMENT
27 Sunday Oct 2013
Posted in EMERGENCY MANAGEMENT
22 Tuesday Oct 2013
Posted in EMERGENCY MANAGEMENT
Click here to listen to the September 17, 2013 interview. Transcript below is for “The Navy Yard Shootings: Coordinating A Response And Healing Hearts”
25 Thursday Jul 2013
“There’s an app for that” has become a very popular phrase–and not just from teenagers. Apps (short for applications) are programs designed to run on smartphones and/or tablets–even without a phone or data connection. In January, Apple announced that they have sold over 40 billion apps for their iOS devices (such as the iPhone and iPad). Clearly apps are a huge part of information-sharing and reaching our target population, here are some reasons why your agency should considered designing and developing your own app:
In June 2013, the Pew Research Center reported its findings that 56% of Americans have smartphones capable of downloading apps–up from just 35% in 2011. Additionally, the number of Americans without a cell phone is down to just 9% of the population. According to research from New Relic, the average smartphone has over three dozen apps (forty-one to be exact) and the average smartphone user checks her phone 150 times per day with 127 minutes per day spent on apps. It is estimated that by the end of 2013, there will be 1.82 billion active smartphones globally and within the next two years, almost 100 billion apps are predicted to have been downloaded by smartphone users.
Unlike a webpage, when content or information is updated in an app, the app can send an alert to the smartphone user to acknowledge the update (also called “push” alerts). During an emergency, it is possible to also send direct messages to users through the app. While not robust enough for a sole means of emergency notification, push alerts or push notifications can be one of the tools emergency managers use for notifying the public. Additionally, if your agency includes plans in its app, app users will always have the most up-to-date plans. When posted on the internet, users can sometimes stumble upon an older version of a plan that has been saved by a search engine or re-posted by local groups, etc. With an app, there is unfiltered access to the most up-to-date information (without the fear of cached versions of older plans recirculating during an emergency).
When disconnected from wifi or wireless data feeds, apps can still function because they have the ability to save information to a user’s smartphone from the previous time an update was downloaded or a connection was available. If your agency wishes to provide any type of guidance for constituents if wireless connectivity is degraded, apps are a good solution. For items like evacuation routes, shelter guides, checklists, and other steady-state documentation, the apps can include those documents and simply update any of the documentation when the user connects to the internet–yet still maintains a copy on the user’s smartphone for when internet connectivity is unavailable.
Since almost all smartphone users keep their phones nearby (how else would they be able to check their phones 150 times per day?), the smartphone is a better targeted device for distributing information than a laptop or desktop computer. Apps are built for ease of use–especially in transit or on the go. For emergency managers, our intended audience during an emergency are those constituents who can be empowered with the right information to help themselves and their community. Oftentimes, information is needed immediately–not when a person can find a computer nearby. Thus, the app is a perfect way of presenting actionable, executable information in a timely manner in a reliable format.
As the operating systems (OS) of mobile devices become more advanced, apps are becoming better integrated with other programs on smartphones, such as maps, the address book, GPS, text messaging, and social media. The benefit of emergency management apps would be the deeper integration with other platforms. In a large-scale disaster, an emergency management app could open up a smartphone’s maps app to plot a course to safety. Once safe, an emergency management app could recommend using social media (rather than a phone call–which ties up limited bandwidth) to let family members and friends know that the user is safe. Deeper integration with reminders, calendar appointments, and other future mobile platform developments can serve to promote preparedness, enhance dynamic, safe responses, and encourage more robust recovery from disaster.
While not every emergency management agency is ready to release their own app, agencies such as Washington, DC’s Homeland Security and Emergency Management Agency (HSEMA), Virginia’s Department of Emergency Management (VDEM), and even FEMA have already released apps for specific use during emergencies. Will your agency be next?
24 Wednesday Jul 2013
Posted in EMERGENCY MANAGEMENT
Click the link below or the cover on the left to download the revised FCD-2 (dated July 2013)
26 Wednesday Jun 2013
Posted in EMERGENCY MANAGEMENT
When emergency managers are able to utilize the latest technology tools and resources, we are afforded new opportunities to enhance resiliency and truly engage with the communities we serve. In recognition of the pace of technology transformation and its impact on our work, the International Association of Emergency Managers established the Emerging Technology Caucus or “IAEM-ETC”. The IAME-ETC seeks to shepherd in new technologies through educational outreach, and help practitioners increase awareness, acceptance and proficiency. Per our mission, we will “research, evaluate, and make recommendations on new and innovative technology as they pertain to emergency management processes, and disseminate best practices to the broader emergency management community”. Caucus members are comprised of practitioners from a myriad of unique disciplines with representation from all levels of government, non-profit organizations, and the private sector.
The use of technology in emergency management is rapidly evolving; two of the most recent examples are the crowd-sourced web-based FEMA Think Tank, and the mass proliferation of social media. Initiatives such as these are why the focus of the IAEM-ETC is intentionally broad, some of our areas of interest are: investigating methods of integrating social media into the Incident Command System, examining the impact of the federal Integrated Public Alert and Warning System or “IPAWS” on local notification systems, leveraging mobile technology to manage incidents and reach impacted populations, and identifying cost-effective strategies for implementing new technology systems. It is our collective hope that this work will enhance preparedness by facilitating greater acceptance and proficiency with next generation technologies. We are honored to be part of the IAEM community and look forward to your input on which technology concepts you would like us to explore.
26 Wednesday Jun 2013
Posted in EMERGENCY MANAGEMENT
From an outsider’s perspective, Sandy Hook Elementary school did everything right. They practiced active shooter drills, locked the campus doors every morning after 9:30 AM, and relied on an access control system. As the nation’s schools review their physical security and safety procedures following the horrific incident in Connecticut, it is important for emergency management not solely rely on protection strategies, but to consider prevention techniques as well.
As defined in the National Preparedness Goal, prevention includes “capabilities necessary to avoid, prevent, or stop a threatened or actual act of terrorism…” On the other hand, protection includes the capabilities to “safeguard the homeland against acts of terrorism…” Since the Federal definition of terrorism requires that the act include political motivations, active shooter incidents usually cannot be labeled terrorism. While active shooting incidents may not neatly fit the definition of terrorism, active shooter incidents are criminal acts intended to cause terrorism in their randomly chosen victims. Clearly, our best defenses are not limited to infrastructure protection and additional physical security.
to avoid, prevent, or stop a threatened or actual act of terrorism…” On the other hand, protection includes the capabilities to “safeguard the homeland against acts of terrorism…” Since the Federal definition of terrorism requires that the act include political motivations, active shooter incidents usually cannot be labeled terrorism. While active shooting incidents may not neatly fit the definition of terrorism, active shooter incidents are criminal acts intended to cause terrorism in their randomly chosen victims. Clearly, our best defenses are not limited to infrastructure protection and additional physical security.
Technological advances in security are often the easiest solutions to identify following a horrific killing spree. However, a significant root cause of these active shooting incidents appears to be mental illness. This means that the emergency management field is forced to intersect with mental health awareness, physical security, and proper training and outreach to our constituencies. It is no longer enough or acceptable to simply rely on physical security and active shooter response training to keep everyone safe.
Similar to how emergency management has partnered with the public health field, it is also time for the emergency management field to partner with mental health professionals to develop awareness briefings and active shooter prevention programs and seminars.
According to a US Secret Service report, over 90% of “attackers engage in some behavior prior to the attack that cause others–school officials, parents, teachers, police, fellow students–to be concerned”. From the same report we learn that in “nearly two thirds of attacks, more than one person had information about the attack before it occurred.”
fellow students–to be concerned”. From the same report we learn that in “nearly two thirds of attacks, more than one person had information about the attack before it occurred.”
These two statistics reveal that in the majority of cases, potential active shooters either told someone about their planned attack or engaged in behavior that might have signaled their intent. This means that the majority of active shooter incidents can be prevented—but it requires training for non-mental health professionals to understand the signs and to feel comfortable reporting a potential active shooter to the proper authorities.
While we normally consider active shooters to be “loners” or isolated individuals, the statistics show that active shooters typically tell others about their plans. In one case, a student told over 20 other people of his plans—yet no one reported it to law enforcement or school officials. When the student came to school, the US Secret Service report explains, “24 students were on the mezzanine waiting for the attack to begin.” It is unbelievable to think that active shooters are indicating their intent to conduct an attack and those that hear of the attack are not informing law enforcement—but that is exactly what several case studies regarding active shooters illustrate.
After the Sandy Hook massacre, as schools and other buildings improve their physical protection systems and infrastructure, the emergency management field ought to be pushing for active shooter prevention and mental illness awareness training. We all must be vigilant of the signs and warning indicators that an individual may turn violent and we all must know how to properly report such warning signs.
Many schools have Behavioral Intervention Team (BIT), which monitor reports of concerning or problematic patterns of behavior. However, the BIT has a negative stigma attached to it. For example, as the director of public safety at a community college recently explained, a student stole an item from a classroom and was demonstrating problematic behavior. When public safety officers arrested the student, the professor was advised to submit the student’s conduct for BIT review. The professor declined to report the behavior to the BIT because the professor explained that she did not want the student to get into more trouble. In most institutions, BIT are non-punitive and cannot lead to a student receiving additional punishment. Yet, the stigma surrounding mental illness and BIT are major factors for warning indicators and problematic behavior to go unreported or under-reported.
As the emergency management field reflects on recent and past active shooter incidents and pledges to do more to stop future attacks, our field must elevate prevention campaigns to work seamlessly with additional protection strategies. It is time for the Whole Community to embrace prevention and protection strategies; our safety depends on it.
25 Tuesday Jun 2013
Posted in EMERGENCY MANAGEMENT
For the first time, the IAEM conference last month debuted the Crisis Technology Center (CTC). Throughout this year’s IAEM conference in Orlando, the Emerging Technology Caucus (ETC) set-up and staffed the CTC to answer technology questions, provide support for the IAEM2Go mobile application (or app), and to generally improve understanding and adoption of social media and other emerging technology in the emergency management field. Members of the ETC wore green ribbons that proclaimed “Techspert”, with the intent being to invite conference goers to feel comfortable approaching the Techsperts with technology questions.
The CTC provided the opportunity for Techsperts to converse with their emergency management colleagues about social media, new technology, and share lessons learned and best practices. Of course, as mentioned in a many sessions during this year’s conference, social media was a very popular topic and tended to be the most popular question posed to the Techsperts. The ETC had a total of fourteen Techspert volunteers comprising of a 50/50 split between Emerging Technology Caucus and Student Caucus members. The Techsperts are experts from various fields and unique disciplines, such as local emergency management, federal public health, and even regional volunteer coordination.
The booth provided conference goers with several benefits, such as live tracking of Hurricane Sandy, a visual presentation of the most popular tweets about the conference, and an open forum for technology questions. Social media, particularly Twitter, was even more prolific this year. At the end of the conference, at least 1,057 tweets were sent using conference hashtags. Indeed, a several conference goers even “live-tweeted” sessions. “Live-tweeting” is defined by Twitter as “to engage on Twitter for a continuous period of time—anywhere from 20 minutes to a few hours—with a sequence of focused Tweets.” While attending certain sessions, some Techsperts would rapidly post several tweets describing the session, pointing out important points, and providing other data and statistics to anyone following the session remotely.
Aside from introducing the concept of Twitter (since the majority of Techsperts were graduates of the National Disaster Preparedness Training Center social media course), Techsperts could help agencies and individuals establish maintain both their personal profile and Facebook page for their agencies. Emergency managers who lacked familiarity or comfort with social media were given an opportunity to meet with Techsperts who have experience using social media in disasters.
Additionally, the Emerging Technology Caucus–having just celebrated its one-year anniversary–used the Crisis Technology Center as an opportunity to build camaraderie and team unity. Since most of the ETC members only know each other through social media, getting a chance to meet in person is somewhat of a surreal experience. Oftentimes it is surprising to meet an individual that seems ordinarily reserved on Twitter, only to discover that the person is actually a social butterfly (or vice versa). Affectionately called the “Nerd Herd”, through service to the IAEM community, the ETC became a stronger team.
As Mackenzie-Anne Kelly, a volunteer Techspert and member of the Emergency Technology Caucus, explains, “At the end of the conference, it was clear that the Crisis Technology Center bridged gaps across all levels of emergency management and helped create a common understanding that everyone in each level of emergency manager plays an important role during any phase of emergency management.”
25 Tuesday Jun 2013
Posted in EMERGENCY MANAGEMENT
In the past few years, the role of social media during emergent incidents has become increasingly more prominent. This past October, as super-storm Sandy struck New York City, several tweets provided cause for concern. “BREAKING: Confirmed flooding on [New York Stock Exchange]. The trading floor is flooded under more than 3 feet of water”, said one tweet. “ Con Edison has begun shutting down all power in Manhattan”, read another. Those tweets, along with dozens of other posts and rumors, turned out to be completely false. Another example, documented by the Chicago Tribune, included “fake images… including a picture of a storm cloud gathering dramatically over the Statue of Liberty and a photoshopped [image] of a shark lurking in a submerged residential neighborhood”. For most social media users, sharing a picture over multiple systems and platforms is as simple as tapping a few buttons, the speed at which data can be shared within a global network of users can facilitate the spread of hoax messaging.
Con Edison has begun shutting down all power in Manhattan”, read another. Those tweets, along with dozens of other posts and rumors, turned out to be completely false. Another example, documented by the Chicago Tribune, included “fake images… including a picture of a storm cloud gathering dramatically over the Statue of Liberty and a photoshopped [image] of a shark lurking in a submerged residential neighborhood”. For most social media users, sharing a picture over multiple systems and platforms is as simple as tapping a few buttons, the speed at which data can be shared within a global network of users can facilitate the spread of hoax messaging.

 Upon initial inspection, the quality of some doctored photos are stunning and even the sharpest skeptic can mistake a fake picture as genuine. Fortunately, visual examination is only one method of verification. Reverse image search engine TinEye, provide a better gauge of image authenticity. By uploading or linking the suspicious image to http://www.TinEye.com, users are able to see where that image, or a similar version, has been posted in the past. In a few clicks, communications and situational awareness teams can quickly debunk a bogus picture post.
Upon initial inspection, the quality of some doctored photos are stunning and even the sharpest skeptic can mistake a fake picture as genuine. Fortunately, visual examination is only one method of verification. Reverse image search engine TinEye, provide a better gauge of image authenticity. By uploading or linking the suspicious image to http://www.TinEye.com, users are able to see where that image, or a similar version, has been posted in the past. In a few clicks, communications and situational awareness teams can quickly debunk a bogus picture post.
The need for an accurate representation of the scale and impact of a disaster is crucial, not just to first responders, but also to the public who needs current and factual information in order to regain a feeling of control over the situation. At the Federal level, FEMA’s external affairs personnel began to take notice of the misinformation and began to formulate a plan to combat the more prominent hoaxes. Peter Herrick, a FEMA external affairs specialist, explained that “we began to see reports…which stated that FEMA was hiring volunteers at a rate of $1000 per week”. After confirming that those reports were fake, Mr. Herrick explained that the reality set in that “…there would be numerous scams and misinformation about FEMA and it’s programs that would circulate as a result of this large-scale disaster.”

FEMA’s rumor control strategy was simple and effective at identifying rumors, disproving them and providing factual information in their place. Speculations and questionable reports were posted on a designated website ( http://www.fema.gov/hurricane-sandy-rumor-control ); falsehoods were clearly marked with a red “X” while facts were marked with a green check-mark. An added benefit to the system, was the ability for media outlets to vet citizen-reports, which in turn, further assisted in quashing misinformation and preventing accidental rebroadcasts of false accounts.
It is an unfortunate reality that some individuals will take advantage of the vulnerable and needy following a crisis. Numerous scamshave been well-documented and FEMA has been equally dedicated in their efforts to prevent their recurrence. For instance, one scam profiled in a FEMA press outlined how “a resident was asked by phone to send the caller, posing as a FEMA representative, a $250 check to process a $5,000 disaster assistance check from FEMA.” In fact, the caller was not associated with FEMA and the entire episode serves as a warning to others to be on the alert for scam artists masquerading as disaster assistance volunteers and staff.
Super-storm Sandy is one of, what will undoubtedly be dozens of, disasters that will test our rumor control tactics. For local emergency managers, it can be heartening to see partners at the Federal level leading the charge to develop and test these new methods. As technology evolves and the public becomes increasingly reliant upon mobile devices and social media for real-timenews before, during, and after an incident, so too must our ability to quickly combat misinformation and communicate the truth.
24 Monday Jun 2013
Posted in EMERGENCY MANAGEMENT
Perhaps due to the location of Super Storm Sandy and the incredibly media savvy and connected population in New York and New Jersey, social media quickly became the story as images of flooding and damage were immediately publicized. In Sandy’s aftermath, international groups of emergency managers focusing on the use of social media in disasters discussed some of the lessons learned. As Jenny Sokatch, of the DHS Lessons Learned Information Sharing system, explains, “These chats (as well as the #smem hashtag) helped us identify creative ideas and innovative practices used during Sandy that we may not have originally included in out lessons learned information sharing system, LLIS.gov.”
The following key concepts were refined from the discussions:
Nationally, many agencies seem to solely use social media to push information to the public rather than utilizing social media to engage and communicate with the community, especially during emergencies. Agencies often warn citizens not use social media to report emergencies. During Sandy, the New York City Fire Department tweeted: “Do not tweet emergency calls. Please call 911.” Other agencies even go so far as to block two-way communication on social media.

FDNY Social Media Manager Emily Rahimi received praise for her tireless social media presence during Hurricane Sandy
In practice, when people are desperate and faced with a busy signal on 9-1-1, they turn to social media for assistance. The question is whether agencies are prepared for handling emergencies reported by social media. Are agencies listening? Are they re-directing information, providing just-in-time safety information or even life-saving information, have a process to pass along messages to dispatch or re-evaluating their policies to better handle the issue of emergency information coming through social media? As we advance towards a text- and video-capable 9-1-1 system, these issues are likely to become even more important. Many agencies need to re-evaluate their policies for handling emergency or urgent messages and might consider establishing a plan to listen and route messages through their EOC or even dispatch systems.
Agencies that were quick to react on social media were able to send out their most critical messages prior to major cell towers losing power (and thus failing). Agencies must be prepared to deliver messages quickly, which may mean re-evaluating an agency’s approval process or require pre-approved messages pre-scripted in advance of a disaster. Additionally, many agencies attached links to social media messages that directed readers to basic and not mobile-friendly web pages. Mobile device-friendly webpages optimize graphics to make information clearer and easier to read; these pages can be independent mobile websites or use responsive design so that webpages scale in proportion to a user’s screen size.  When power and wireless internet resources are limited, the best solution to ensure speedy delivery of messages may mean sending several messages in a row that communicate the message rather than pointing the user to a website. Additionally, when planning recovery operations, ensure proper agreements are in place to quickly mobilize Cells On Wheels and Mobile Charging Stations.
When power and wireless internet resources are limited, the best solution to ensure speedy delivery of messages may mean sending several messages in a row that communicate the message rather than pointing the user to a website. Additionally, when planning recovery operations, ensure proper agreements are in place to quickly mobilize Cells On Wheels and Mobile Charging Stations.
As citizen groups increase social capital through online networking, agencies must engage the community in a variety of social media platforms and respond to a need they see in the community because they are listening to social media. In order to do so as a field, we may need to be more aware of how to reach and communicate with these networked groups to help everyone achieve the same goal. Independent groups can do phenomenal things and, in a major disaster, coordinating with community stakeholders will always be challenging.
During Sandy, the “Occupy” movement re-branded itself as “Occupy Sandy” and put their social media muscle to work. It was through their knowledge of social media and listening to the needs of the community that they were able to coordinate their response. In fact, newspapers reported their novel use of an Amazon.com wish list to  allow purchases for needed items to be shipped and distributed by volunteers. Agencies that listen intently to the community and engage them in dialogue can motivate volunteer actions. In this way, social media can serve as a force multiplier—not only as a communications tool, but as a response and recovery apparatus.
allow purchases for needed items to be shipped and distributed by volunteers. Agencies that listen intently to the community and engage them in dialogue can motivate volunteer actions. In this way, social media can serve as a force multiplier—not only as a communications tool, but as a response and recovery apparatus.
Communicating the severity of disasters using only words takes a talented wordsmith, but the old adage that “a picture is worth a thousand words” was quite literal during Sandy. As people sought to emotionally connect with their friends, neighbors and family members they sent photos via social media. Two social media platforms, Pinterest and Instagram, gained instant notoriety in sharing digital images. Both platforms have the ability to search for images tagged by a user, and Instagram uses the same hashtag system as Twitter, which makes images easier to find.
Even if your agency is not using these tools to share images, training social media staff on how to conduct searches of images can be useful for situation status updates, common operating picture, and the general condition as reported by residents of a community and survivors of a disaster.
While most people share photos to tell their story of the disaster, there were other nefarious individuals who used photos to create rumors. Use of photos and verification techniques was mentioned in last month’s IAEM article, however it is useful to note that reverse photo tools are available to identify misleading and patently false photos. Agencies should be prepared to verify photos and have a system in place to communicate the authenticity of a photo, or any rumor for that matter. Agencies should consider practicing the use of reverse look-up photo tools to identify the source of an image. Identify an agency policy or resource of where and how to communicate false pictures and how you may use authentic pictures as actionable intelligence. It is worth noting that social media is in fact social and the majority of users take great offense at intentional dishonesty. As such, they will often come to the aid of an agency calling out erroneous information. Do not fear incorrect information in social media, but do have a plan to report rumors and communicate accurate information quickly.
Every disaster includes limited resources and a need to effectively distribute the resources that are available. During Sandy, fuel supply was limited and it was difficult for survivors to identify gas stations with adequate supply . 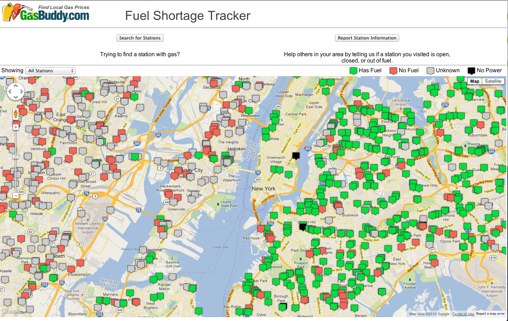 Utilizing a variety of crowd sourced methods, inducing data from apps, Google mapping, and others, workers and volunteers were able to map data of available resources and keep it updated with timely and relevant information. Agencies should consider working with information technology support and GIS partners to identify mapping solutions for the types of disaster scenarios in your agency’s plan. Free mapping tools and crowdsourcing programs, such as Google Crisis Response mapping, Ushahidi, and Creative Commons are the future of emergency management.
Utilizing a variety of crowd sourced methods, inducing data from apps, Google mapping, and others, workers and volunteers were able to map data of available resources and keep it updated with timely and relevant information. Agencies should consider working with information technology support and GIS partners to identify mapping solutions for the types of disaster scenarios in your agency’s plan. Free mapping tools and crowdsourcing programs, such as Google Crisis Response mapping, Ushahidi, and Creative Commons are the future of emergency management.
Social media plans and policies should be reviewed frequently to ensure that your agency’s intentions for using social media during disasters matches the needs of the community. There is a great deal of information on Sandy available from Lessons Learned Information Sharing (www.llis.dhs.gov), where you will find additional reports on technology used during the storm.
23 Sunday Jun 2013
Posted in EMERGENCY MANAGEMENT
This is a presentation I have given several times detailing research about active shooters in schools and correcting the assumption that active shooters are unpreventable. With the right training and awareness, the majority of active shooter attacks are preventable.